Hybrid Cloud Security: Challenges & Best Practices To Overcome Them

Hybrid Cloud Security: Challenges & Best Practices To Overcome Them
The distribution of data is becoming more and more efficient through hybrid cloud systems. Enterprises get the perks of both private as well as public cloud environments along with the secure data management framework.
Moreover, these frameworks are compatible with the mobile OS and web applications so that businesses can manage cloud-based operations more efficiently. However, the challenges regarding these frameworks are increasing with their evolution.
IT companies and enterprises are making every possible effort to optimize their data centers and bring maximum productivity.
This distribution of IT workloads is based on a tradeoff between cost, performance, and dependability of service. Hybrid cloud computing offers the opportunity to strike an optimal tradeoff—but it also faces significant security challenges.
Here are they:
1. Visibility and control
As users begin to present foundation past actual machines and virtualization—for instance, a blend of public mists, for example, Azure, AWS, and Google with private mists, OpenStack—multifaceted nature, and danger develop at an outstanding rate.
This makes it substantially more trying for organizations to view and control all the appropriate frameworks that make up the foundation. This is particularly valid for directors who are physically checking for security and consistency—also manual fixing and handling.
2. Supply chain security
It has become a platitude to state that you are just as secure as your most fragile connection—however, you truly are just as secure as your most vulnerable connection. Across an arrangement of hybrid cloud, it very well may be hard to see those connections.
While assessing and executing IT infrastructure frameworks and systems, organizations must know where the solutions that they are utilizing came from. It implies having the certainty that the partners they are working with know where their products came from and can guarantee that they are developed safely.
3. Compliance and governance
Cloud technology has now developed to the point that associations in all ventures are utilizing it at some level. All things considered, the crossbreed framework presents exceptional difficulties for associations in the medical care, monetary, government, and other controlled areas.
Probably the greatest test comes not from anyone guideline, but rather from the way that numerous organizations are still physically verifying that they are agreeable and meeting custom or administrative security baselines for security consistency and evaluating necessities.
4. Data security
Security challenges are continually active, however hybrid cloud push-ups unpredictability. Across progressively perplexing and broad hybrid cloud conditions, data can be harmed in stabilized as well as sharing mode.
No single defensive usage can forestall all potential strategies for a data security threat, since similar data might be stored constantly or being shared across various resources for different purposes.
Another way users can guarantee information security in a hybrid cloud system is to search for arrangements that execute standard assurance measures.
When cloud security norms are followed appropriately, a hybrid framework will help to improve a company’s IT security norms. Be that as it may, security should be an obvious bit of your general hybrid cloud arrangements, or you may be attracting new threats without finding a way to relieve them.
Risk assessment and monitoring
Reference:
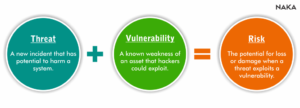
Threats confronting cloud networks develop quickly as cybercriminals find better approaches to attack the organization’s weak endpoints. To comprehend the cloud network environment at any instance, you need a precise threat handling profile.
This data is basic to proactively play out the fundamental threat confronting exercises. It is accordingly imperative to follow these accepted procedures:
- Assess and evaluate the danger of confronting private cloud management activities.
- Build up a danger profile and recognize the assets needed to handle the security challenges inside the accessible spending plan.
- Keep all product and organization end-face in the know regarding security patches.
- Screen network traffic conduct for dubious exercises.
- Utilize progressed AI-based organization observing advances that relate network conduct with potential danger exercises confronting the cloud.
Maintaining the cloud security of your infrastructure is a big task, and until you achieve success, you need to keep assessing and optimizing the systems.
Hybrid Cloud Security Control Planning
Achieving the most adaptive approach for perceivability and control with hybrid cloud security solutions need in-house ability, cutting-edge innovation, and adequate assets to oblige the developing volumes of security-delicate data.
This also includes the applications running inside private cloud organizations in-house. In this unique circumstance, the accompanying prescribed procedures are valuable:
1. Determine data computing requirements
A reasonable cloud migration technique should represent business development and private cloud versatility assumptions, which are ordinarily more costly than public cloud options.
2. Aim for shadow IT practices
Shadow IT solutions might be open to access sensitive and crucial business information. These solutions should be under the vision of your hybrid cloud systems with complete visibility and control.
3. Consider SIEM solutions
Public cloud arrangements and SaaS applications offer restricted perceivability and control to their clients. Progressed Security Information and Event Management (SIEM) arrangements might be needed to see how to open cloud arrangements connected with your sensitive information.
4. Understand compliance
Extra consistency measures might be required depending on the kind of information and the cloud organization model. A hybrid cloud model may present extra difficulties and openings for security consistency that ought to be recognized and tended to.
5. Verify & monitor data security
It is possible that the cloud administration system offers adequate perceivability and control into cloud frameworks, however, the scaling development might not legitimize the investments.
Be that as it may, it may not be possible to move information and applications to another seller—merchant lock-in—because of significant expense or innovation merging issues. Hence, it is necessary to lock your information and applications in with a single cloud services provider.
Prioritize, and focus on automating one thing at a time at each layer of the stack. That way, you’re more secure than you were yesterday while instilling better practices for a more secure tomorrow.



